Date
May, 2014
Conference
IEEE CCECE 2014, Toronto
Paper download rank
Download from IEEE Xplore Download Conference Presentation
Authors: Solely authored
Abstract: Since its introduction in 2009, Bitcoin, an open source, peer to peer, digital crypto currency has been growing in popularity and wide spread use. Growing attention, recognition by major financial institutions and high valued currency units (BTC) ascertains Bitcoin to a sturdy and ever increasing choice of currency. A public transaction log called the “Blockchain” keeps records of all committed transactions and Bitcoin ownership details, that is, addresses derived by cryptographic keys. Bitcoin mining, a process which results in the generation of new Bitcoins, is performed by miner operators for reception of incentives in the form of Bitcoins. This mining process is essentially operations of SHA-256 hashing of values in search of a hash digest smaller than a specific value. Once this winning hash has been discovered, a new block to Blockchain is added and BTC incentives are furnished by the Bitcoin network to the miner. This paper discusses methods of performing Bitcoin mining on non-custom hardware which results in contextually faster mining by combined usage of computing elements within machines in mining networks, both illegal and legal.
Languages
Tools
(Google Scholar) Citations earned:
- Tschorsch, Florian, and Björn Scheuermann. “Bitcoin and Beyond: A Technical Survey on Decentralized Digital Currencies.”
- Morisse, Marcel. “Cryptocurrencies and Bitcoin: Charting the Research Landscape.” (2015).
- Quan-Liang Lin. “Using Proof-of-Assignment to solve NP problem:A platform for Vapor Computing” (2015).
- Kumkum Gupta, Sparsh Agrawal, Ashrut Bharadwaj. “Dependability of Bitcoin in E-Commerce” (2015)
- de Koning, Patrick, and W. P. Weijland. “In hoeverre is het Bitcoin systeem een piramide systeem?” (2015)
- Carlos Domingos Vaz Lampreia Horta Martins, “Parallelization of the LU Decomposition in Heterogeneous Systems” (2015)
- Lawrence of J.Trautman, “Is Disruptive Blockchain Technology the Future of Financial Services?” (2016)
- Holk, Eric. Region-based Memory Management For Expressive Gpu Programming. Diss. Indiana University (2016)
- Weber, Martin. “Cryptocurrencies and the Block Chain.” (2016)
- Kim, Sungwook. “Group bargaining based bitcoin mining scheme using incentive payment process.” Transactions on Emerging Telecommunications Technologies (2016)
- TEXTBOOK: Protocols for Secure Electronic Commerce, Third Edition, Mostafa Hashem Sherif, ISBN 9781482203745, (2016)
- Jesse Yli-Huumo, Deokyoon Ko, Sujin Choi, “Where Is Current Research on Blockchain Technology?—A Systematic Review” (2016)
- Conoscenti, Vetr, De Martin, “Blockchain for the Internet of Things: a Systematic Literature Review” (2016)
- Schmidt, Rainer, et al. “Benefits from Using Bitcoin: Empirical Evidence from a European Country.” International Journal of , Management, Engineering, and Technology (IJSSMET) 7.4 (2016): 48-62.
- John Liu, “Bitcoin : A Co-word Analysis”, 6th Economics & Finance Conference, Paris.
- Godsiff, “Bitcoin: Bubble or Blockchain?”, 9th KES International Conference 2015.
- BOOK: Agent and Multi-Agent Systems: Technologies and Applications, 2016
- Notheisen et al (2017). “Breaking Down The Blockchain Hype – Towards A Blockchain Market Engineering Approach”. In Proceedings of the 25th European Conference on Information Systems (ECIS) 2017 (pp. 1062-1080). ISBN 978-989-207655
- 19,20 (Awaiting links)
Accolades:
- This paper is currently the most downloaded paper of the conference with a monthly hit count more than twice the average hit count of papers in the conference.
- This paper was nominated for being “Award Quality” (see screenshot of in-EDAS feedback)
- Featured in a university textbook on Secure Electronic Commerce (See citation#11)
- Featured in a state of academy research compilation by Brett Scott (Alternate financial explorer, author, and writer for TheGuardian, Wired; has made appearances on BBC)
- I wasn’t required to pay the registration fee of $750, and was waived mandatory of the conference.
This project came from the basic ideas used in my first 2 papers. That is, using the CPU and GPU together for purposes. This paper doesn’t require readers to know how the entire Bitcoin system actually works, but, it’s best if you knew atleast knew where the “brute force” comes in. I’ll be extremely brief here, the “mining” process involves repeatedly performing SHA256 hashing on random values until the hash digest is of a certain “quantity”. This paper focuses on this “mining”
Now, there used to be a time when Bitcoins were mined by solo miners. This was was back in the late 2000s. As computing power and the numbers of miners increased, the “difficulty factor” for Bitcoin mining increased as well (this is a consequence of having to ensure that Bitcoins are minted once every 10 minutes only; not lesser or greater than 10 minutes. Bitcoin transactions are “recorded” when a new block is generated every 10 minutes. These are things which are very fundamental to the Bitcoin system, do read up on it to understand this. Trust me, it’s quite simple). To keep up with increasing difficulty factors, miners started mining together in pools. The put “most solo miners” out. Here’s an (unnecessary) picture to give you an idea of what: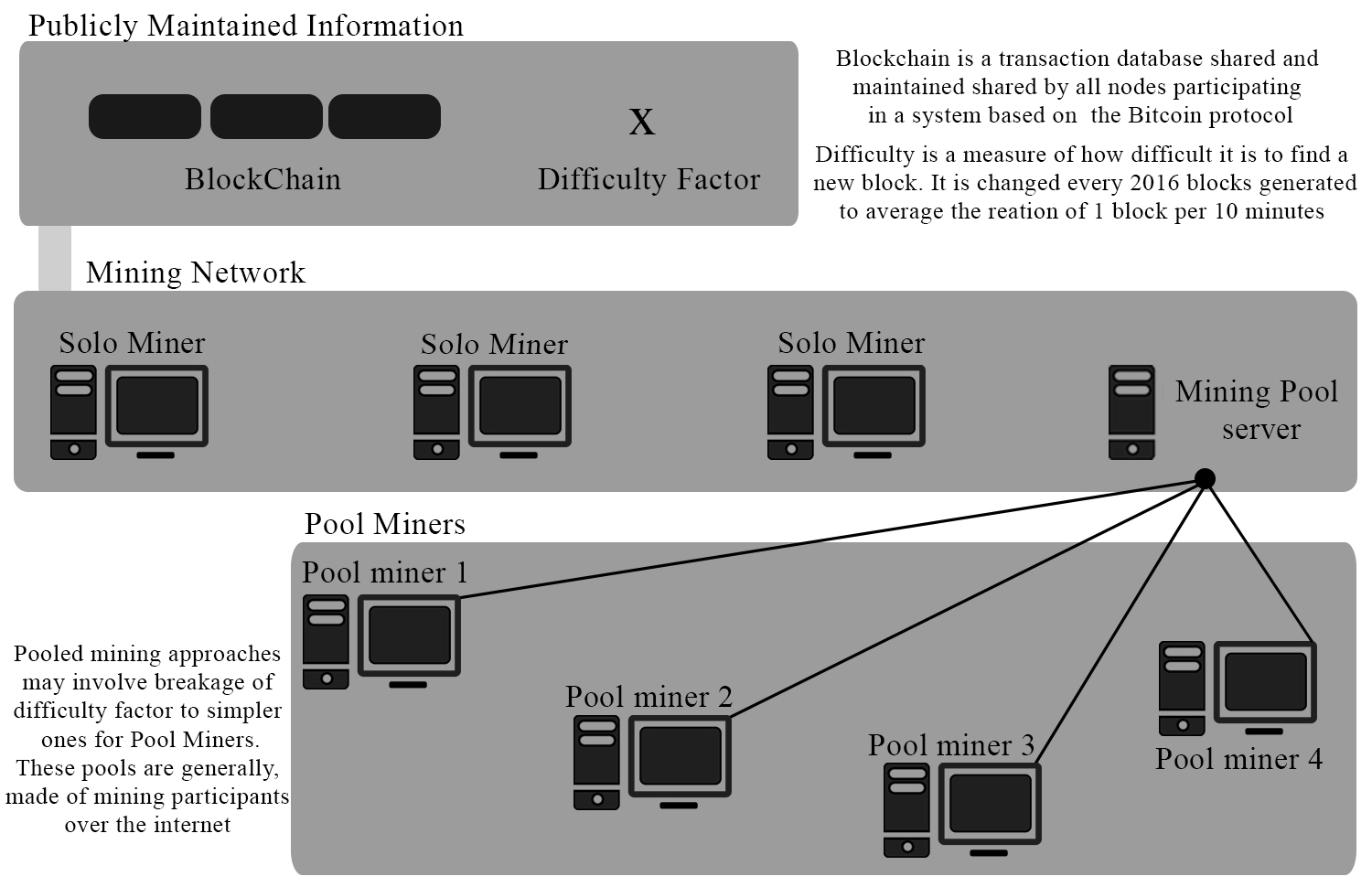 Apart from using insanely powerful GPUs for Bitcoin mining, people now use AISICs or FPGAs to get insanely high hash rates with the added benefit of minimal power consumption as compared to using GPUs. The obvious way to get “higher” hash rates would be to invest in dedicated hardware as these. Note that these devices are generally EXTREMELY expensive as compared to GPUs.
Apart from using insanely powerful GPUs for Bitcoin mining, people now use AISICs or FPGAs to get insanely high hash rates with the added benefit of minimal power consumption as compared to using GPUs. The obvious way to get “higher” hash rates would be to invest in dedicated hardware as these. Note that these devices are generally EXTREMELY expensive as compared to GPUs.
Now, let’s see how one can “get highers hash rates”. Remember, whenever I talk about getting higher hash rates, I’m talking about its relative contexts. There’s probably no way in which a solo miner could muster enough power to compete against pool mining. But, what could be done in pool mining to get higher hash rates? There isn’t anything “smart” about everyone getting AISICs or FPGAs. Ofcourse, they’d boost the pool’s entire hash rate, but, at an obvious cost. Apart from common sense stating that if people could “just do it”, they’d have already done it.
So, what if we could get just a little more from each of these miners in a mining pool? With the same setup that they’ve got. No investments whatsoever (other than perhaps, a little power consumption). My other two papers used this method of simultaneous usage of the CPU and GPU for processing tasks.
Using the CPU and GPU together isn’t exactly difficult. It’s quite simple. Remember that this is simple brute force, so, synchronization and other complicated techniques or whatever, is of no use here. In fact, you could just grab a CUDA for beginners book, and started coding this program within 2 or 3 days at max. Ofcourse, this assumes you’ve got a general idea of multi threading and stuff, atleast on the CPU. Here’s a diagram showing how this looks like. Look for yourself, it’s really simple.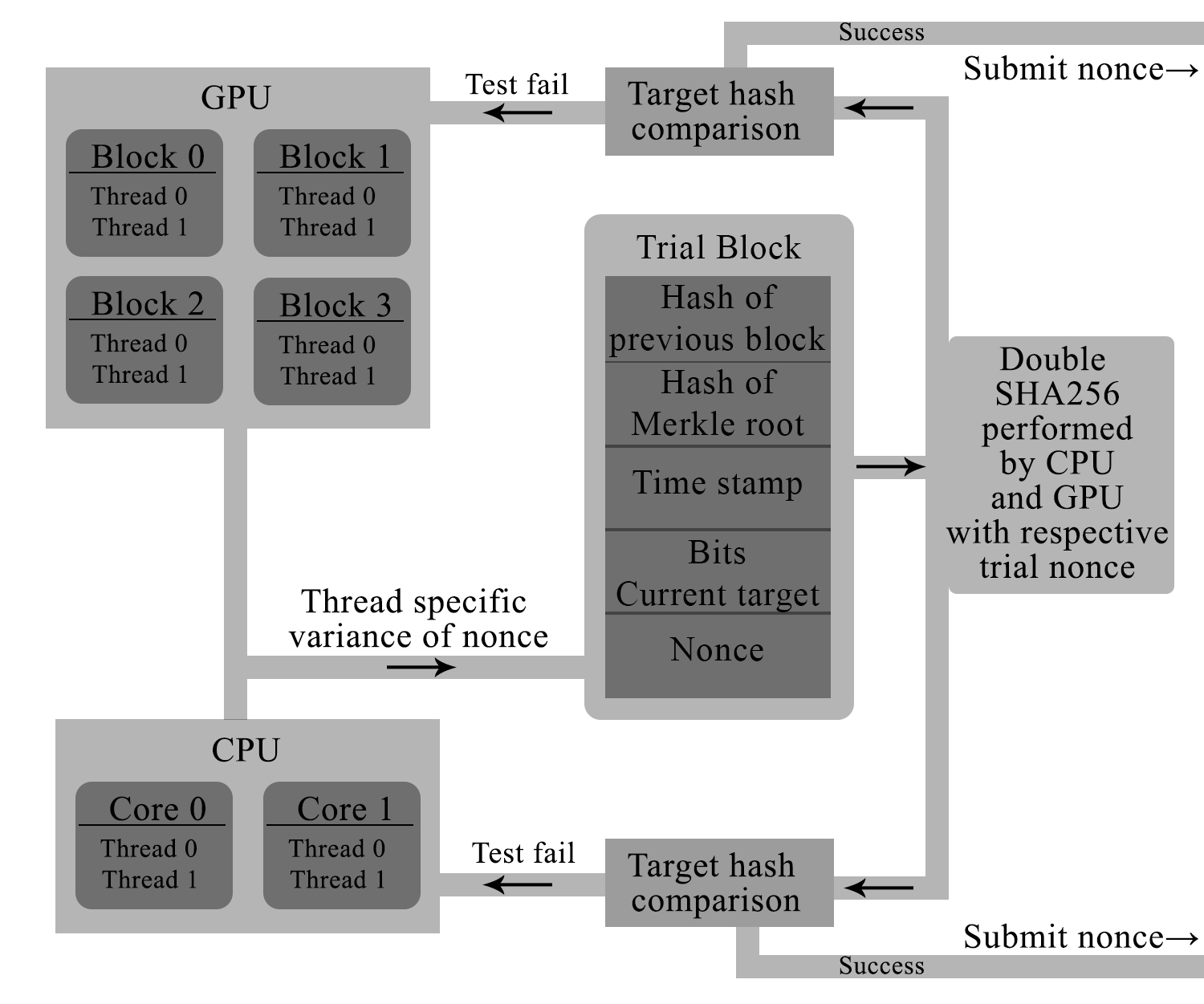 Before I began work on the miner, I knew I’d certainly get atleast a slightly greater total hash rate. I was concerned about how good this boost for. This was because the SHA256 algorithm was a little more “complex” than MD5, the ones I’ve worked without before. I tested the miner on 2 of my machines: C1 and C2. C1 had CPUs Intel I7-2600K @ 3.3 GHz, 4 Cores, 8 logical processors and GPUs NVIDIA GTX 550 TI. C2 had CPUs Intel I5-3210M @ 2.5 GHz, 2 cores, 4 logical processors. These machines were chosen to analyze ratio differences in hash rates obtained in a high end computer with an intermediately powerful graphics cards and a normal home computer with a standard graphics card and processor.
Before I began work on the miner, I knew I’d certainly get atleast a slightly greater total hash rate. I was concerned about how good this boost for. This was because the SHA256 algorithm was a little more “complex” than MD5, the ones I’ve worked without before. I tested the miner on 2 of my machines: C1 and C2. C1 had CPUs Intel I7-2600K @ 3.3 GHz, 4 Cores, 8 logical processors and GPUs NVIDIA GTX 550 TI. C2 had CPUs Intel I5-3210M @ 2.5 GHz, 2 cores, 4 logical processors. These machines were chosen to analyze ratio differences in hash rates obtained in a high end computer with an intermediately powerful graphics cards and a normal home computer with a standard graphics card and processor.
RESULTS:
The results were analyzed in terms of increase in hash generation rate upon combined usage of CPU and GPU as opposed to sole usage of the GPU. Hash rates were observed along the first few seconds of mining till the rates stabilized.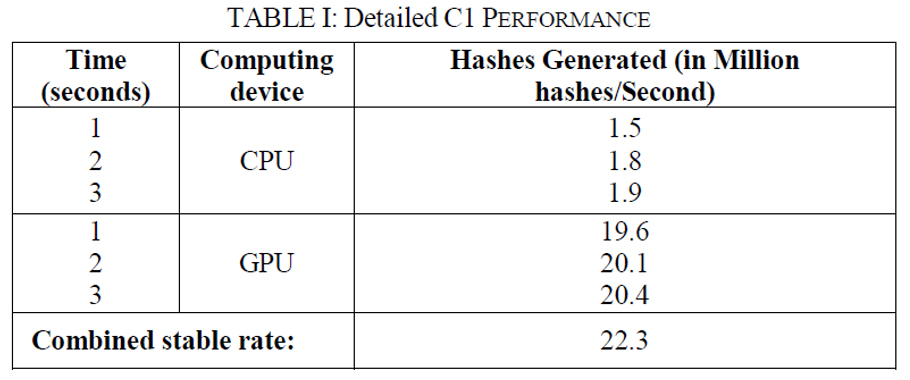
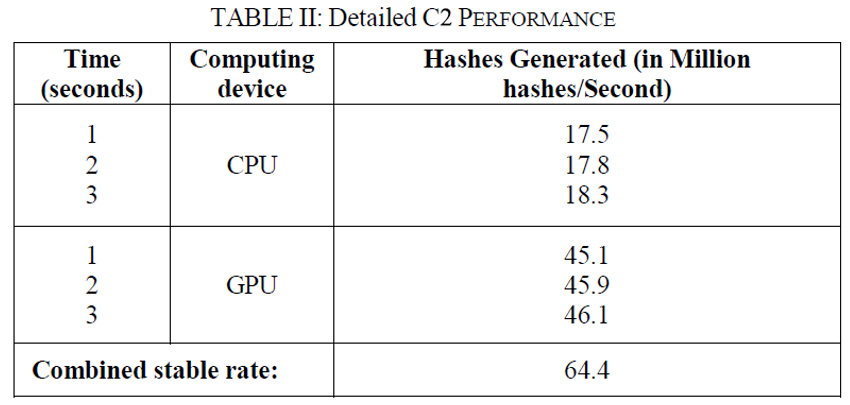
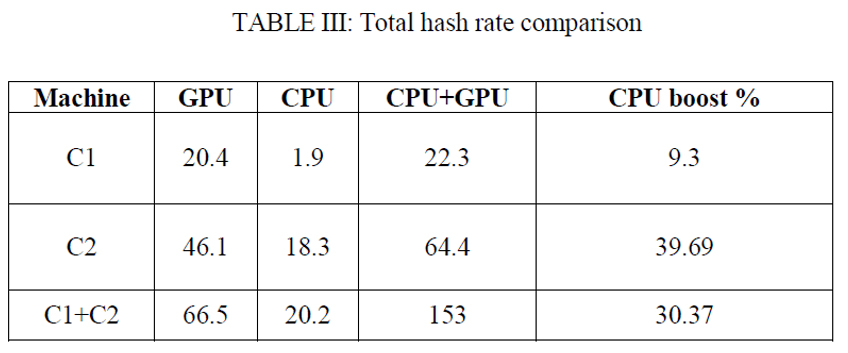 I concluded that these boost rates were pretty good for machines such as mine. One would expect the ratios to fall in gaming machines since the GPUs are generally extremely powerful when compared to their CPUs (for mining). But, the gaming PCs having power CPUs as well (I’m talking a comparison in terms of ratios).
I concluded that these boost rates were pretty good for machines such as mine. One would expect the ratios to fall in gaming machines since the GPUs are generally extremely powerful when compared to their CPUs (for mining). But, the gaming PCs having power CPUs as well (I’m talking a comparison in terms of ratios).
Now, what can one infer from these results? When considering an entire mining pool, for example, a totally of 27,682 miners, online on a public miner in December 2013, constituting a total hash rate of 2,172 Trillion hashes per second, it is inferred that that each miner averages a little more than 4 billion hashes per second. It is unlikely that each and every one of the miners had used an FPGA). The pool, therefore, consists of a highly imbalanced and irregular distribution of miners with a minority of them contributing to a large fraction of the total hash rate.
The results established in this paper show how standard hardware miners in large mining pools such as this, could quite significantly add to the overall hash rate. This can be roughly quantified by assuming a mere 1000 of these users to be possessing hardware capable of hash rates between the hash rates of test machines C1 and C2. Taking an average of 35 Million GPU hashes per second and 15 Million CPU hashes per second, 1000 miners can be expected to output an additional 15 Trillion hashes per second, which is a considerably large boost when seen in terms of actual hashes generated per second.
THE BOTNET IMPLICATION:
This is a theory of mine. It’s a implication from the results concluding that using a number of CPUs together in a pool could quite significantly boost overall hash rates.
Owing to its comparatively lower value ($30, December 2013) most miners are tempted to contribute to Bitcoin mining instead of Litecoin mining, which uses scrypt hashing instead of Bitcoin’s SHA256. A botnet herder could take advantage of the comparatively smaller number of miners and hence, smaller total hash rates, and go on to be a relatively dominant Litecoin miner, which is very improbable in the case of Bitcoin mining. Furthermore, if a botnet comes to possess enough computing power to attribute to 51% or more of the entire hash rate, an attacker could even modify a past bock, undo and then redo “Proof-of-Works” of blocks and eventually surpass the work of honest miners. This is, however, not very possible in the Bitcoin network as achieving 51% of the entire mining hash rate is extremely impractical on any botnet, even with ones having millions of bots.