10th grade, 2007.
10th grade, 2007.
This program was created to infiltrate a Cyber Cafe Management Systems called “Easy brow”. It was popular in Saudi Arabia, atleast during my growing up years. I once discovered that they the program makers didn’t write any secondary measures to check whether their process was shut down by external means. The server just assumed that the client machine had timed out and shut down. My program could be put in a disk and when inserted into a cyber cafe’s client machine, would automatically start and find out the target process, suspend it and minimize it. Also, it would return all locked resources to the user. (I never used the program to “steal” from cafes. I only did this out of interest; a challenge to myself”)
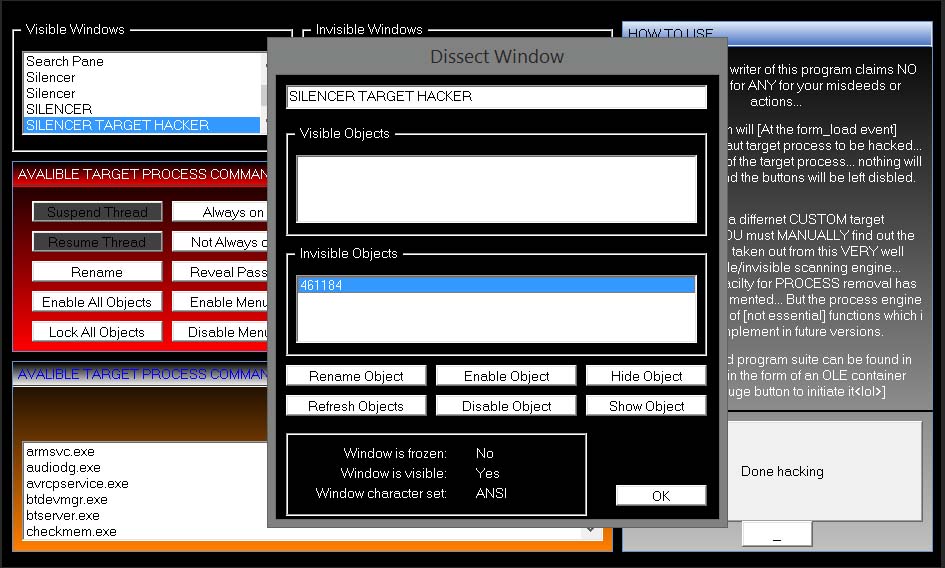
The program had a dual purpose. Upon start-up, it would look for the Cyber Cafe management software’s Client process (this is pre-programmed). Once it finds the process, it suspends it and releases the keyboard hooks held by the program. These keyboard hooks stopped the user from being able to press Control+Alt+Delete, Control+Escape, Alt+Tab etc, essentially, anything that could help the user to close or bypass the client’s login screen. The second feature is used to expand the user’s freedom once the client has been done away with. The user would find himself in an account with many things disabled, for example, the windows Shell. My program would manually start up the Windows shell. This can’t be done by using the Task manager because it would disabled by (simple) registry entries. My program would reset these registry entries, too. The task manager would still be limited, though. But, the user could use my program to escalate himself to have the task manager’s “run” privileges by “hacking” into the task manager’s objects and forcibly changing it’s the “End task” or “Run” button’s property to “enabled”. (This can’t be done in new versions of windows. I don’t know when this stopped working, but, it worked in windows XP and Vista, too, I believe).
Apart from this, I included a number of other features that the user might be required to use. For example, I included a window hider so that user could quickly hide the software if his computer was going to be inspected by the Cafe’s management. Also, I included other features pertaining to process and memory manipulation (mostly trivial ones, I confess, I was a kid, I wanted to make the program look “as cool” as possible).
Another bit of confession here. As noticeable, this program entirely isn’t exactly as difficult as it may seem. The whole thing is just a smart way of calling process and window related windows API, meaning, a smart sequence of taking things from one function and then using them in another function to achieve something unique.
Lastly, before I show you the screen shots. I’m telling you again, I was a 15 year old kid back then. My idea of a “cool program” then was black, cluttered, complicated looking, abstractly colored, “hacker themed” programs full of words like “hacker” and so on. So, spare me 😉
Screenshots:
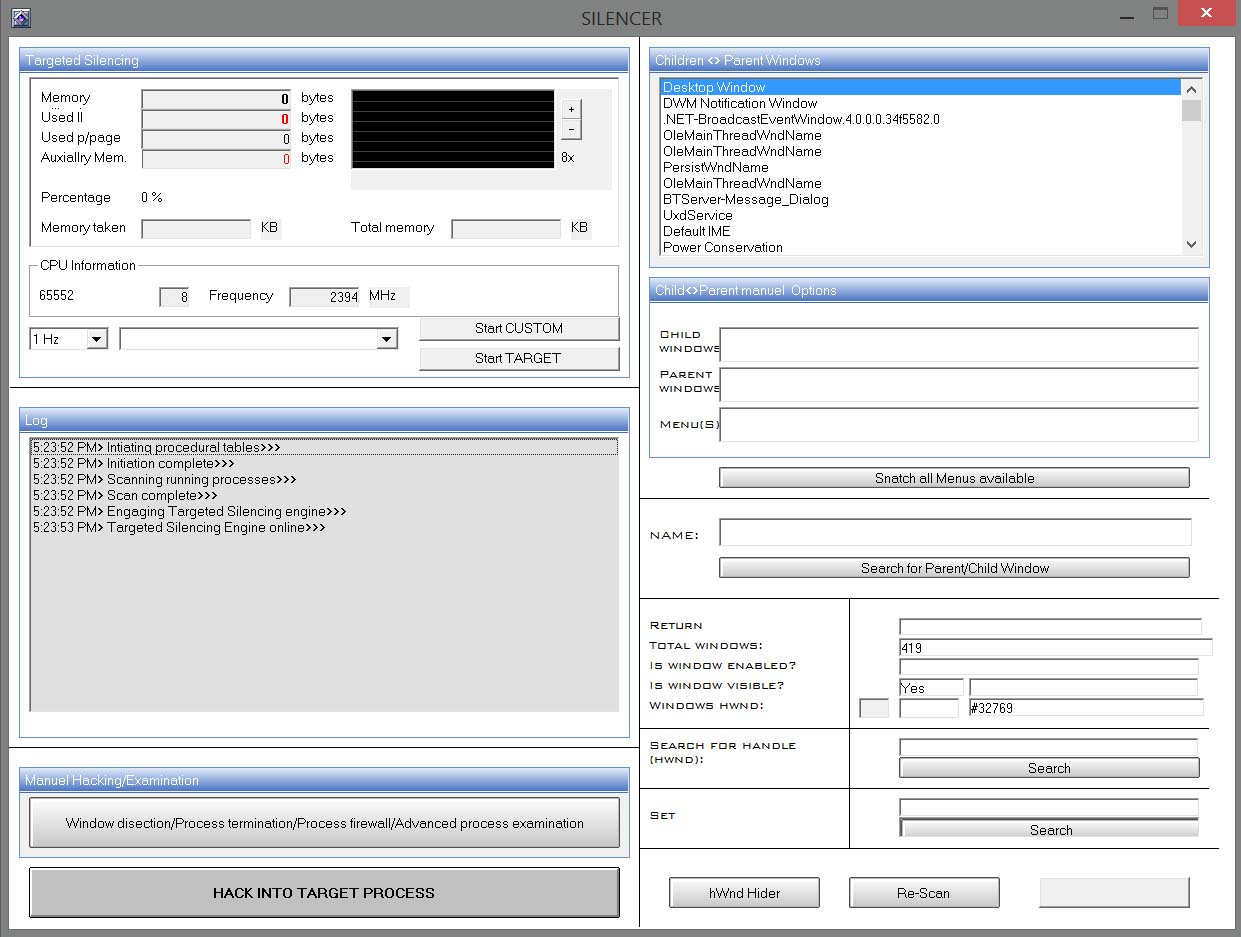
The main screen of the program. Again, I am embarrassed at how the program looks and with the words “hacking” all over the place