January, 2017. Personal project
The National Security Agency (NSA) holds a Code Breaker Challenge each year. Participants from across the world get to reverse engineering and “break” software during tasks in the challenge. This year (2016), there were 6 tasks. This program was coded to solve tasks of the challenge (NSA Code breaker challenge 2016). You can modify parameters according to variables used in your binaries.
For use in solution/answers of Tasks:
Task 3,Task 4,Task 5, and Task 6. (Click here to view my progress. Update: The profile progress link for 2016 participants doesn’t seem to be working anymore, since this year’s competition has started. You can find the publicly view-able results of 2016 here. You can see that only one person has finished Task 5 from the University of Florida (that’s me!), by scrolling to the bottom and searching for “University of Florida” in Task 5. Click here for a screenshot)
The code (at places) might not be too “clean”, I’m sorry for that. After all, I made this program just to “get things done”, and not for demonstration of efficient coding 😉
Highlights:
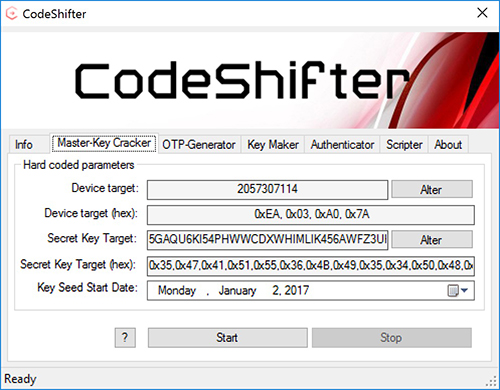
- Multi-threaded Brute forcing of master key
- OTP generation
- Decryption of .enc.key files
- Encryption of forged key files
- Quick set-up of test applications
- Automated run-time scripting
Usage:
You’ll need to copy the binaries and key files to the application start-up directory before you can use it. I’ve included the private/public keys that were present in my binaries. I’m not sure if NSA used the same keys for every one else’s binaries. But, in case they did, you can simply use the ones I’ve provided. Note that you’ll HAVE TO COMPILE/RUN in 32 bits ONLY (atleast as far as Windows 10 goes)! Something goes wrong in the brute-force procedure when you do it otherwise (atleast on Windows 10). I haven’t figured out what it is yet, and I don’t intend to do so. If you do figure it out, do let me know!
Screenshots:
I’d love to hear from you if: You just want to say hi, if you found this useful, if you use my code, if you solved task 6, or if you want to team up for 2017’s challenge 😉